
КАТЕГОРИИ:
АстрономияБиологияГеографияДругие языкиДругоеИнформатикаИсторияКультураЛитератураЛогикаМатематикаМедицинаМеханикаОбразованиеОхрана трудаПедагогикаПолитикаПравоПсихологияРиторикаСоциологияСпортСтроительствоТехнологияФизикаФилософияФинансыХимияЧерчениеЭкологияЭкономикаЭлектроника
E-mail and Newsgroups
The connection of the networks throughout the world forms what is known as the Internet. Networksall over the world are connected to the Internet using electronic devices known as routers. The routers decide which route on the Internet a particular signal should take to get to its destination. Users often pay a monthly fee to a type of company known as an Internet Service Provider, to provide them with Internet connection. A variety of services are controlled using a system of server computers at various locations throughout the world.
Electronic mail, which has come to be known as e-mail is one of the most popular services on the Internet. 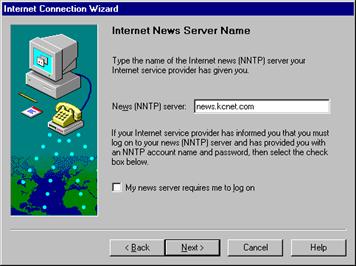 E-mail allows users to send digital messages to storage areas known as mailboxeson server computers where they can be read by other users. Each user has ones own e-mail address, which determines where their e-mail is stored. A typical e-mail address might have the following components: username of identifier, @, server name, type of organization, country (e.g. locka@pesto.co.uk)*
E-mail allows users to send digital messages to storage areas known as mailboxeson server computers where they can be read by other users. Each user has ones own e-mail address, which determines where their e-mail is stored. A typical e-mail address might have the following components: username of identifier, @, server name, type of organization, country (e.g. locka@pesto.co.uk)*
The e-mail message has two main parts known as the header and the bodyof the message. The body contains the message itself, the header reveals the identity of the recipient and the sender, the date it was sent, and the subject title of the message.
The message header should include at least the following fields:
From: The e-mail address, and optionally the name of the author(s). In many e-mail clients not changeable except through changing account settings.
To: The e-mail address(es), and optionally name(s) of the message's recipient(s). Indicates primary recipients (multiple are allowed).
Subject: A brief summary of the topic of the message. Certain abbreviations are commonly used in the subject, some of which are automatically inserted by the e-mail client, including Re: ("in the matter of"), FW: (forward), FYI: (for your information), I: (information), and EOM (end of message, used at the end of the subject when the entire content of the e-mail is contained in the subject and the body remains empty).
Date: The local time and date when the message was written. Like the “From:” field, many email clients fill this in automatically when sending. The recipient's client may then display the time in the local format and time zone.
Message-ID: Also an automatically generated field; used to prevent multiple delivery and for reference in In-Reply-To:. 
Note that the “To:” field is not necessarily related to the addresses to which the message is delivered. The actual delivery list is supplied separately to the transport protocol, SMTP, which may or may not originally have been extracted from the header content. The “To:” field is similar to the addressing at the top of a conventional letter which is delivered according to the address on the outer envelope. Also note that the "From:" field does not have to be the real sender of the e-mail message. One reason is that it is very easy to fake the "From:" field and let a message seem to be from any mail address. It is possible to digitally sign e-mail, which is much harder to fake, but such signatures require extra programming and often external programs to verify. Some Internet service providers do not relay e-mail claiming to come from a domain not hosted by them, but very few (if any) check to make sure that the person or even e-mail address named in the “From:” field is the one associated with the connection. Some Internet service providers apply e-mail authentication systems to e-mail being sent through their MTA (Mail Transfer Agent) to allow other MTAs to detect forged spam that might appear to come from them.
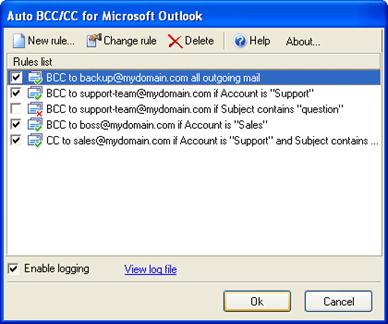 Bcc: Blind Carbon Copy; addresses added to the SMTP delivery list but not (usually) listed in the message data, remaining invisible to other recipients.
Bcc: Blind Carbon Copy; addresses added to the SMTP delivery list but not (usually) listed in the message data, remaining invisible to other recipients.
Cc: Carbon copy; many e-mail clients will mark e-mail in your inbox differently depending on whether you are in the “To:” or “Cc:” list.
Content-Type: Information about how the message is to be displayed, usually a MIME type.
In-Reply-To: Message-ID of the message that this is a reply to. Used to link related messages together.
Precedence: commonly with values "bulk", "junk", or "list"; used to indicate that automated "vacation" or "out of office" responses should not be returned for this mail, e.g. to prevent vacation notices from being sent to all other subscribers of a mailing list.
Received:tracking information generated by mail servers that have previously handled a message, in reverse order (last handler first).
References: message-ID of the message that this is a reply to, and the message-id of the message the previous was reply a reply to, etc.
Reply-To: address that should be used to reply to the message.
Sender: address of the actual sender acting on behalf of the author listed in the From: field (secretary, list manager, etc.).
X-Face: small icon.
Formatted text, spreadsheets, sound files or video files can be attached to mail messages.
One of the biggest problems in e-mailing is spam. To prevent e-mail spam, both end users and administrators of e-mail systems use various anti-spam techniques. Some of these techniques have been embedded in products, services and software to ease the burden on users and administrators.  No one technique is a complete solution to the spam problem, and each has trade-offs between incorrectly rejecting legitimate e-mail vs. not rejecting all spam, and the associated costs in time and effort. Anti-spam techniques can be broken into four broad categories: those that require actions by individuals, those that can be automated by e-mail administrators, those that can be automated by e-mail senders and those employed by researchers and law enforcement officials.
No one technique is a complete solution to the spam problem, and each has trade-offs between incorrectly rejecting legitimate e-mail vs. not rejecting all spam, and the associated costs in time and effort. Anti-spam techniques can be broken into four broad categories: those that require actions by individuals, those that can be automated by e-mail administrators, those that can be automated by e-mail senders and those employed by researchers and law enforcement officials.
Sharing an email address only among a limited group of correspondents is one way to limit spam. This method relies on the discretion of all members of the group, as disclosing email addresses outside the group circumvent the trust relationship of the group. For this reason, forwarding messages to recipients who don't know one another should be avoided. When it is absolutely necessary to forward messages to recipients who don't know one another, it is good practice to list the recipient names all after "bcc:" instead of after "to:".  This practice avoids the scenario where unscrupulous recipients might compile a list of email addresses for spamming purposes. This practice also reduces the risk of the address being distributed by computers affected with email address harvesting malware. However, once the privacy of the email address is lost by divulgence, it cannot likely be regained.
This practice avoids the scenario where unscrupulous recipients might compile a list of email addresses for spamming purposes. This practice also reduces the risk of the address being distributed by computers affected with email address harvesting malware. However, once the privacy of the email address is lost by divulgence, it cannot likely be regained.
Groups of users that share a special interest can subscribe to free newsgroups on the Internet. Users subscribe by registering their e-mail addresses. Subscribers can send plain text messages to a common area on a server computer where all the newsgroup members can read them. In this way, conversations about the special interest can take place between all the members of the group. The name of the newsgroup is made up of different parts separated by dots and indicates the special area the subscribers are interested in (alt; rec; etc).
Here are some examples of the abbreviations of organizations:

 com or со — commercial organization
com or со — commercial organization
edu/ac — education
gov — government
int — international organization
mil — military
net — network provider
org — not-for-profit
Дата добавления: 2014-11-13; просмотров: 455; Мы поможем в написании вашей работы!; Нарушение авторских прав |